The Federal Trade Commission today announced a broad crackdown on scareware scammers accused of using an ancient technology—the telephone—to trick thousands of unsuspecting victims into handing over full access to their Windows PCs. By cold-calling victims and claiming to be from companies like Microsoft, Dell, and McAfee, the scammers directed users to a harmless error log on their computers and told them it was a sign of a serious infection, the FTC said. The alleged scammers went on to charge anywhere between $49 and $450 to "fix" the consumers' computers.
At a press conference announcing six lawsuits filed in US District Court in New York, FTC Chairman Jon Leibowitz said at least 2,400 people—and probably many more—were tricked in this manner. The FTC believes such scams have cost consumers tens of millions of dollars worldwide.
Like a bad Bollywood movie
The FTC played a phone call between one of the defendants and a female victim, who was actually a "highly skilled FTC investigator" playing the role of a clueless computer user. The defendant has an Indian accent, but calls were generally spoofed to appear to be coming from US phone numbers.
Defendant: OK, so now what you need to do, madam, you need to scroll down the page very slowly, very carefully from your end, and you need to just pull it down and tell me if you can see anything else other than the blue color information over there or not. And if you see anything else over there, let me know.
FTC agent: OK. Hold on, I'm doing that.
Defendant: Very careful, all right.
FTC agent. [Pauses]. Ummm, let's see. Oops! Hold on.
Defendant: Uh huh.
FTC agent: Umm, I see something that says "warning"? And something that says "error"?
Defendant: Jesus! Did you see some warnings?
FTC agent: Yeah it says…
Defendant: Hello?
FTC agent: Yeah it says "warning."
Defendant: Madam, it would be my humble request to you, please do not try to click on any of them, OK?
FTC agent: OK.
Defendant: And it would be my request that you keep your mouse pointed away from them, because they are the malicious online infections I was speaking about. Once you click on any of them your computer might even stop responding at any point in time. So be very careful, OK?
FTC agent: OK. I'm not touching the mouse!
Defendant: If you have already seen them this means your computer is also one of those computers which has been infected with the online infections, OK?
Leibowitz cut off the recording there, and said "At one level that's like a bad Bollywood movie. But at another level, that's a serious ripoff of consumers." Such scams have been going on for years, but the operations announced today were particularly widespread.
There were various methods the scammers used to get the users on the phone in the first place. In addition to cold-calling, one of the six defendants "purchased ads on Google, for search terms like McAfee, PC support, and fix MS Office, with pseudonyms and a toll-free number to call," Leibowitz said. The company, named PCCare247, allegedly paid Google more than $1 million for search ads going back to 2010. In one example, searching Google for "Contact McAfee Support" brought up the defendants' phone number and website.
Warning: Everything is working normally
The other five companies allegedly used "telemarketing boiler rooms" to make cold calls, including to people on the Do Not Call list. While mostly based in India, they targeted consumers in the US, Canada, Australia, Ireland, New Zealand, and the UK.
"Pretending to be affiliated with a major computer company, the defendants claimed to have received an automatic notification from the person's computer about a problem," Leibowitz said. "They used Voice over Internet Protocols to seem like they were calling from numbers in the consumer's country, sometimes in the same area code. They told their potential victims to go to their computer, look at a file that shows warning messages—actually these warning messages are just a standard part of the Windows operating system. The messages do not mean the computers are affected with viruses or any other malware."
The "warning messages" come from the Windows Event Viewer, which shows standard messages about the computer's operation. According to Microsoft, "an error is a significant problem, such as loss of data," while "a warning is an event that is not necessarily significant, but might indicate a possible future problem." Scammers allegedly lied to consumers, saying the messages meant hackers were in their computers, and even that their computers might "blow up."
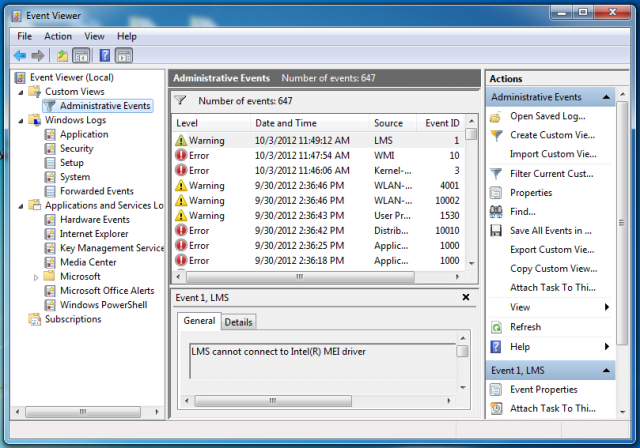
The defendants are charged with "violating the FTC Act, which bars unfair and deceptive commercial practices, as well as the Telemarketing Sales Rule and with illegally calling numbers on the Do Not Call Registry," the FTC said. The FTC charged 14 corporate defendants and 17 individuals, and won a temporary restraining order to freeze $188,000 worth of assets and shut down their operations. This includes disabling Web hosting and phone service.
Microsoft and other computer companies helped the FTC in its investigation, as did authorities in Australia, Canada, and the UK. Canada and Australia also brought legal action against the defendants for violations of their Do Not Call laws.
The names of the corporate defendants charged by the FTC include Pecon Software, Finmaestros LLC, Zeal IT Solutions, Virtual PC Solutions, Lakshmi Infosoul Services, and PCCare247.
In the complaint against Pecon Software in India, the FTC said the scams have been going on since at least 2008. The complaint also describes how the scam unfolds after the users have been tricked into thinking their computers are infected. We quote at length:
Having convinced the consumers that their computers are in imminent danger, the Defendants then direct the consumers to a website and instruct them to enter a code or download a software application to allow the Defendants remote access to the consumers’ computers. Once the Defendants have remote access, they are able to completely control the consumers’ computers and can, for example, move the cursor, enter commands, run applications, and access stored information.
The Defendants then attempt to sell the consumer illusory long-term “security” or “technical support” services and perform unnecessary “repairs,” including installing otherwise free programs, such as trial versions of antivirus programs, and deleting the innocuous files they falsely claimed were viruses. The Defendants charge consumers for these services in an amount ranging from approximately $159 to $299.
The Defendants next direct the consumer to one of several websites they operate in order to pay for the computer security or technical support service. The Defendants’ websites are highly interactive. They purport to allow consumers to chat directly with representatives, leave their contact information to request a call-back, and also browse and pay for various services online. In numerous instances, the Defendants register their websites through privacy protection services that mask their true identity. As a result, consumers are unable to determine the true owner of the website or the fact that the same company operates multiple websites.
If consumers do not agree to pay for the service the Defendants typically apply pressure to the consumers. The Defendants will warn consumers about the harm that will come to their computers if they do not allow the Defendants remote access to fix the computers. Afterwards, the Defendants assert they have fixed the non-existent problems. In reality, Defendants merely charged consumers for repair products and services they did not need.
Tech-savvy Ars readers are unlikely to fall for such a scam. But if you have relatives and friends who lack the necessary dose of skepticism, and they receive unsolicited phone calls from people wanting to fix their computers, they should hang up and report the scam to the FTC or their PC security vendor.
While the scammers seem to just want money, Microsoft Director of Consumer Affairs Frank Torres said their tricks could easily be used for worse.
"What's worse is these scams not only cost victims money in terms of making consumers pay for something they don't really need, or that doesn't happen," Torres said. "But it could also compromise the security of their computers, leaving them vulnerable to malicious software and other attacks."
reader comments
164